9th Floor, Changfeng E Building, North Bank, Lane 168, Daduhe Road, Putuo District, Shanghai.
Tel: (+86)021-51036995
Email: support@datasure.cn
7*24-hour Hotline: (+86)400-821-6995
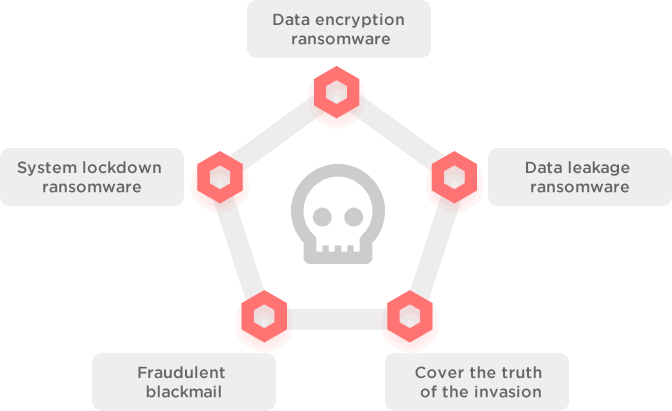
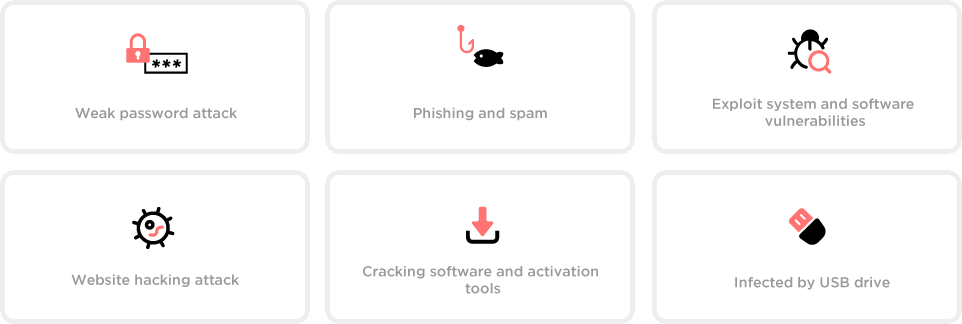
Ransomware is on the Rise
Ransomware and ransomware attacks are a top concern for enterprise customers today. Ransomware is big business and attackers are relentless in their pursuit to develop new, creative ways to infiltrate corporate networks and IT environments to seize data and hold it hostage. The key is to be resilient and to be able to restore at scale.
Ransomware has quickly emerged as one of the most dangerous cyberthreats facing both organizations and consumers, with global losses now likely running to billions of dollars each year. According to relevant data, global ransom ware damage costs predicted to exceed $20 billion by 2021.